Видео с ютуба What Are Rsa Vulnerabilities

Breaking RSA - Computerphile

ECED4406 0x20A - RSA Attacks
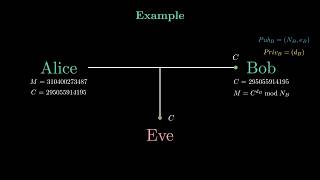
The RSA Encryption Algorithm - How Does It Actually Work + Step-by-Step Example.

The RSA Encryption Algorithm (1 of 2: Computing an Example)

Anatomy of the RSA targeted attack

Some Attacks Against RSA

AI Security Engineering—Modeling/Detecting/Mitigating New Vulnerabilities

Attacks on RSA || Lesson 61 || Cryptography || Learning Monkey ||

RSA Security: Honest Review & User Experience of RSA's Cybersecurity Solutions

DROWN Attack - Decrypting RSA using Obsolete and Weakened eNcryption (TLS Academy)

RSA 2023: Ben Edwards & Sander Vinberg - Evolution of CVEs and Vulnerability Management

Attacks on RSA Signature || Lesson 88 || Cryptography || Learning Monkey ||

What is RSA?

RSA

Introduction to Cryptography: Security of RSA

RSA Security Analytics Demo

The Power of Vulnerability - Brene Brown

How QFT Could Break RSA Encryption Forever

RSA Breach: The Untold Story, Part 1 | Malicious Life podcast

Shor’s Algorithm Explained 🤯 How Quantum Computers Could Break RSA Encryption